How I pwned half of America’s fast food chains, simultaneously.
Also checkout Eva’s blogpost of this event.
With an upbeat pling my console alerted me that my script had finished running, to be precise it was searching for exposed Firebase credentials on any of the hundreds of recent AI startups.
This was achieved through a public list of sites using the .ai TLD and parsing the site data (and any referenced .js bundles) for references to common Firebase initialisation variables.
Production: {
apiKey: "AIza<Insert_Funny_Joke_Here>",
authDomain: "KFC.firebaseapp.com",
databaseURL: "https://KFC.firebaseio.com",
projectId: "KFC",
storageBucket: "KFC.appspot.com",
messagingSenderId: "123456789"
}
My hunch was that in the rush to push their new shiny product, someone would take a shortcut and forget to implement proper security rules.
The hunch was right, and it was worse than I could’ve ever guessed.
Meet Chattr.ai
…The self proclaimed AI hiring system that claims to shave 88% of the time off hiring new people.
They provide their services to a massive number of fast food chains and other hourly employers around the United States, including but not limited to:
- Applebees
- Arbys
- Chickfila
- Dunkin
- IHOP
- KFC
- Shoneys
- Subway
- Tacobell
- Target
- Wendys
The Vulnerability
If you drop the Firebase configuration from the JS bundle into Firepwn, you start out with zero permissions as you can see in the following screenshot.
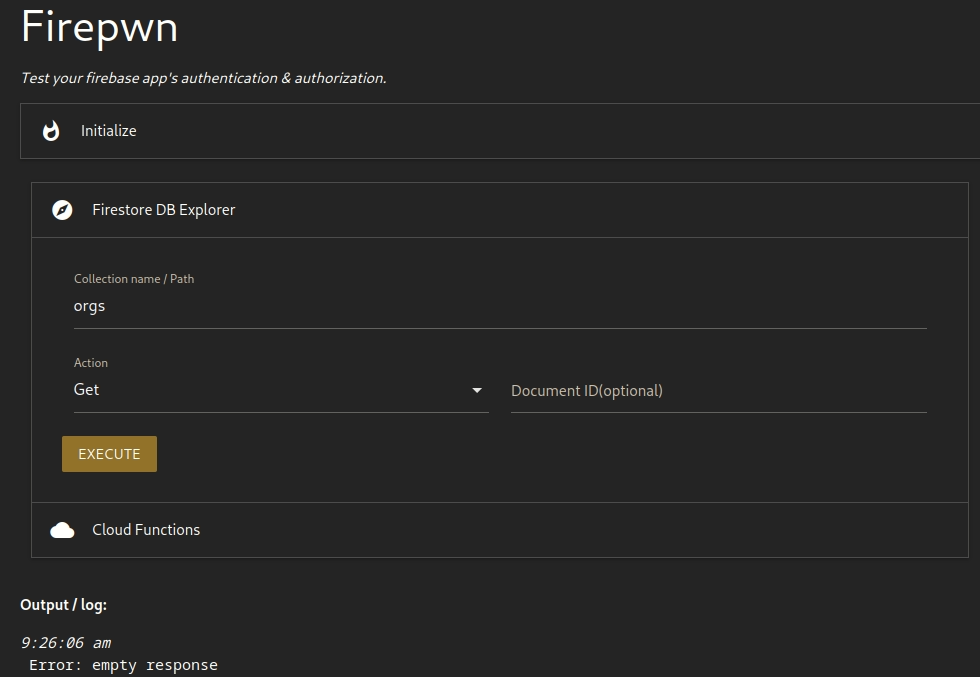
But if you use Firebase’s registration feature to create a new user (you cannot register on their site), you get full privileges (read/write) to the Firebase DB.
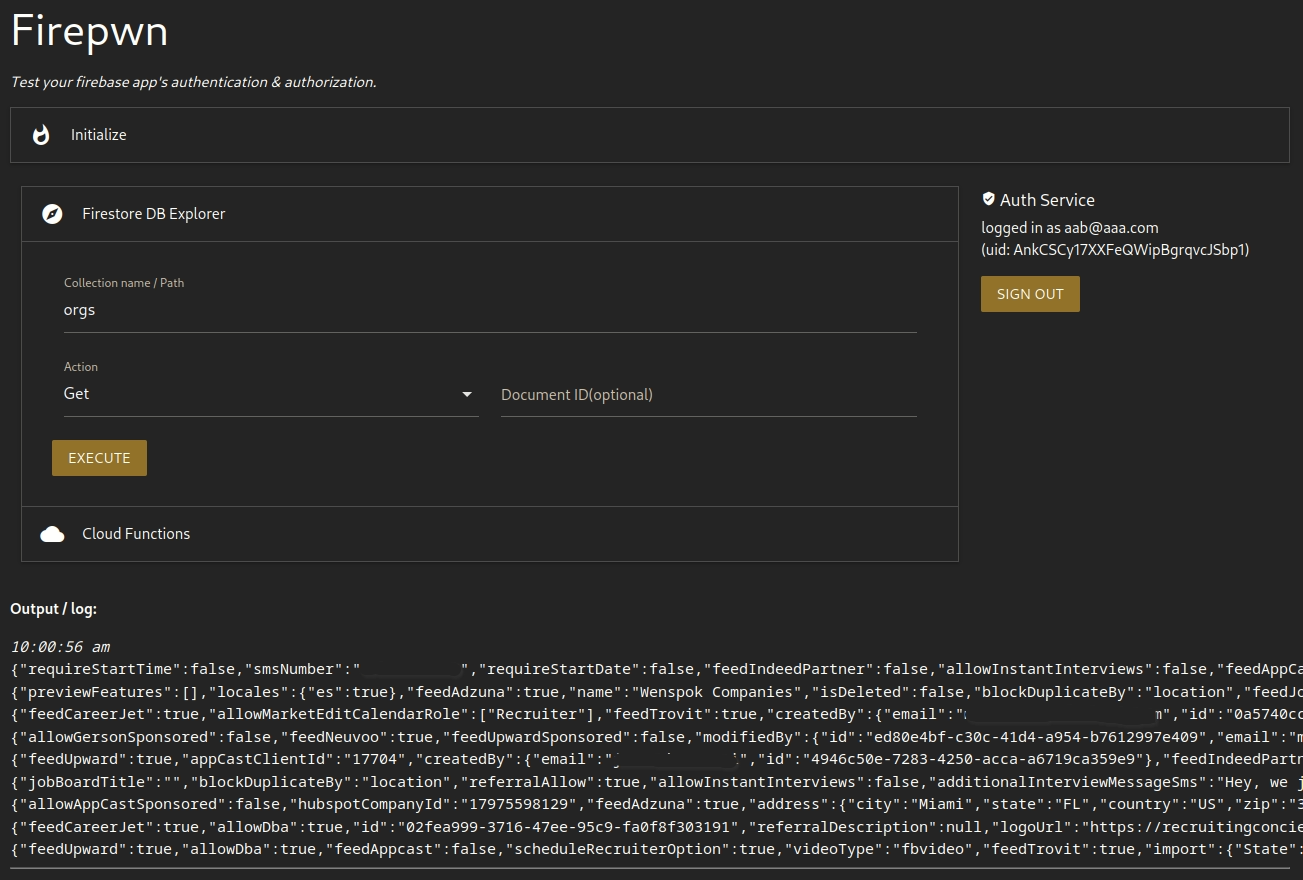
The data it exposes includes and is not limited to:
- Names
- Phone numbers
- Emails
- Plaintext passwords (Only some account’s had exposed passwords)
- Locations of branches
- Confidential messages
- Shifts
For the following:
- Chattr employees
- Franchisee managers
- Job applicants
Timeline (DD/MM)
- 06/01 - Vulnerability Discovered
- 09/01 - Write-up completed & Emailed to them
- 10/01 - Vulnerability patched
- 11/01 - Support ticket closed, no thanks or further contact received despite explicitly requesting it
Credits
To my friends who assisted me with this pentest and responsible disclosure of such
- Logykk
- Eva - https://kibty.town/blog/chattr